
How Automated Posting Tools Improve Efficiency Without Sacrificing Quality
You don’t need to be a marketing guru to understand… How Automated Posting Tools Improve Efficiency Without Sacrificing Quality

You don’t need to be a marketing guru to understand… How Automated Posting Tools Improve Efficiency Without Sacrificing Quality

Protecting sensitive information is paramount in today’s digital age. Whether… How to Password-Protect Your Documents Using Word Editor
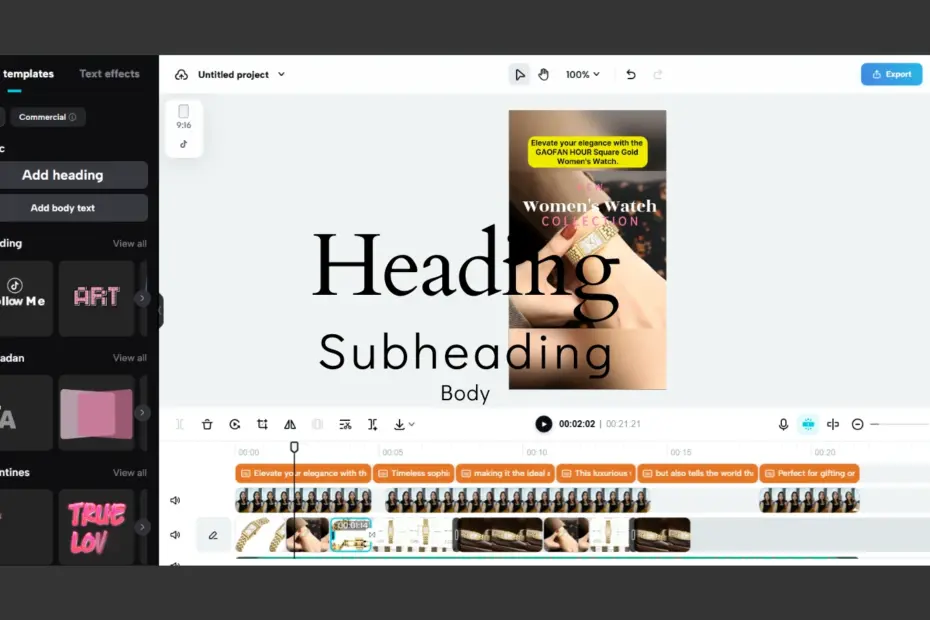
On TikTok and Reels, there’s a general rule: you’re invisible… Before the Beat Drops: Cutting Music Videos to Match Viral Audio Trends
Explore top information technology jobs, including roles in software development, cybersecurity, and data analysis, with career growth insights and opportunities.

Explore top information technology jobs, including roles in software development, cybersecurity, and data analysis, with career growth insights and opportunities.
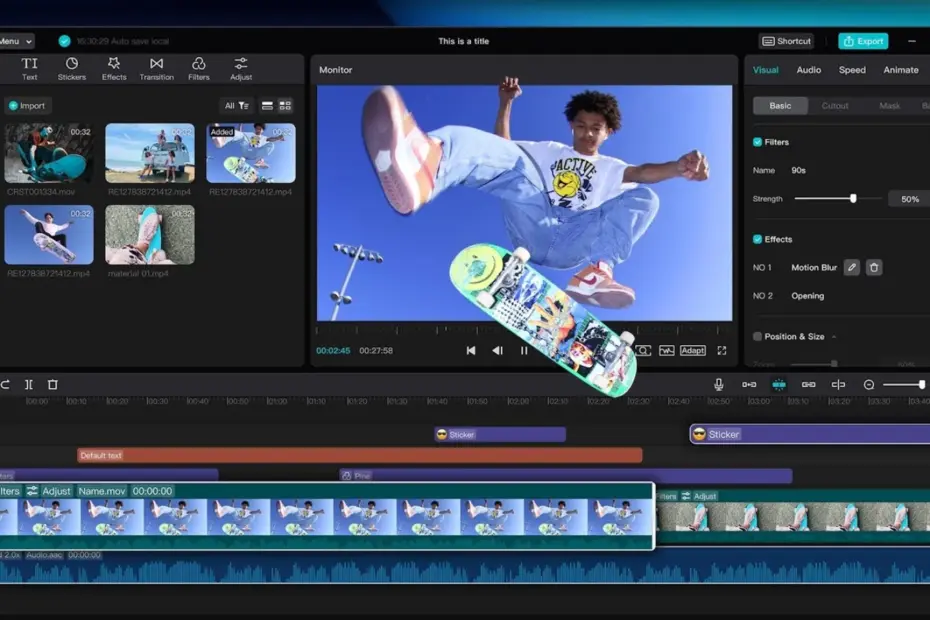
CapCut desktop video editor is a video editing software favorite… Using CapCut Desktop Video Editor’s Speed Curve Tool for Simple Edits

As the healthcare industry embraces digital transformation in 2025, medical… Types of Software Medical Solutions in 2025
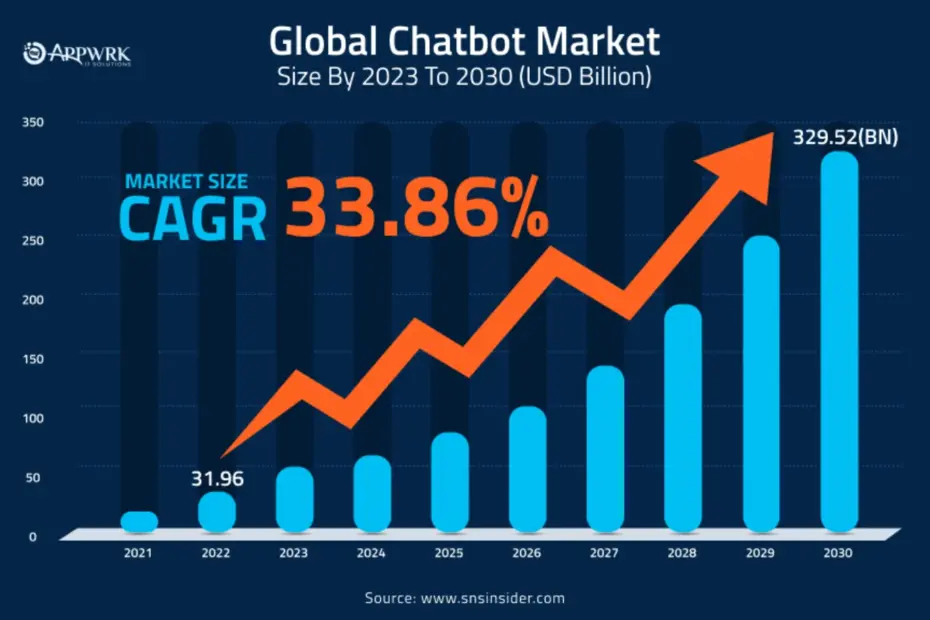
With the rapid advancement of artificial intelligence, chatbots have become… What to Know Before Integrating an AI Chatbot Into Your Website

Why do some brands effortlessly capture attention on social media… Instagram Navigator: Transforming Digital Marketing Strategies in 2025

Imagine your financial transactions discussed in a WhatsApp chat find… Monitor WhatsApp for Secure Financial Transactions and Insights
Have you ever dropped your AI‑generated draft into a checker… Best AI Humanizer Tools In 2025 (Paid&Free)

Looking for a reliable means of communication in 2025? Turn… Best Direct Mail Automation Software Guide 2025

Take a look at your phone. You’ve probably got a… UX/UI Latest Trends for Mobile Apps in 2025

Today, security breaches are in the news almost every day.… Is Virtual Data Room Software Worth It? A Business-Focused Analysis

In an era defined by digital connections, remote work is… How to Safeguard Your Web Development Projects with Remote Teams

Explore how cryptocurrency evolved from a niche concept to a global financial revolution reshaping economies and investment trends.

Tech giants are racing to develop AI tools that can detect AI-generated content, raising new questions about authenticity and digital trust.

AI photo tools are evolving from simple filters to full facial edits, reshaping how we present ourselves and perceive identity online.

AI companions are becoming more intelligent and lifelike, blurring the line between code and connection in digital relationships.
Compare the best signal providers of 2025 based on speed, accuracy, and transparency to choose the right one for smarter, more reliable trading.